INTRODUCTION
The service worker (SW) is an emerging web technology that was introduced to enhance the browsing experience of web users. At the core, it is essentially a JavaScript file that runs in an isolated and privileged context separated from the main web page or web workers. Websites can register a service worker to enable native mobile application features including but not limited to supporting offline usage and sending push notifications. With the help of this technology, traditional websites can now act like native mobile apps or become appified.
Recently, the use of service workers has gained much attention from web developers, security researchers, and even cyber-criminals due to the service worker’s unique capabilities, especially the ability to intercept and modify web requests and responses at runtime. Such capabilities inevitably introduce new factors to web security considerations. As a result, we aim to systematically study both the vulnerabilities and the security enhancement to websites that can come with the introduction of service workers.
Service Worker’s Attack Surfaces
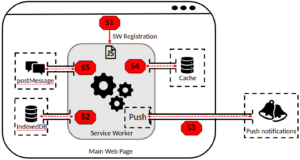
To understand the security implications of service workers, we systematically study the lifecycle and communication channels of service workers. There are mainly five attack surfaces: service worker’s registration lifecycle, IndexedDB, Push message, Cache, and postMessage.
| Attack Surface | Surface Type | Attack Type | Consequences |
|---|---|---|---|
| S1. SW Registration | Lifecycle | SW-XSS | Persistent code execution, sensitive information leakage, phishing attack, etc. |
| S2. IndexedDB | Communication Channel | SW-XSS | Persistent code execution, sensitive information leakage, phishing attack, etc. |
| S3. Push Message | Communication Channel | Push Hijacking | Information leakage such as user locations. |
| S4. Cache | Communication Channel | Side-Channel | Information leakage such as user browsing history. |
| S5. postMessage | Communication Channel | XSS | Code execution, sensitive information leakage, phishing attack, etc. |
Service Worker’s Lifecycle We investigate the service worker lifecycle and uncover a vulnerability allowing cross-site scripts to be executed inside the service worker. We term this novel attack as Service Worker Cross-Site Scripting (SW-XSS) and develop a dynamic taint tracking tool (SW-Scanner) to measure the impact of SW-XSS in the wild.
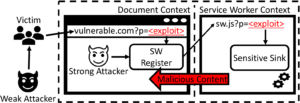
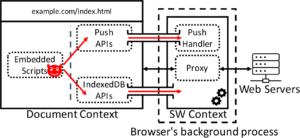
Service Worker’s Communication Channels We analyze the communication channels between the service worker and other web contexts. We identify two vulnerable channels, IndexedDB and Push notifications. These channels can be utilized to launch SW-XSS and push hijacking attacks, which can lead to the privacy leakage of users. We extend an existing taint tracking tool to measure the prevalence of these attacks in top websites.
Service Worker’s Defense
Previous research has mainly focused on utilizing service workers for malicious purposes or compromising a benign service worker. However, the service worker is a powerful web technology that can also be used to enhance the security of websites as a whole. As a result, we explore the possibility of enhancing the service worker against existing attacks (including the five attack surfaces) and use the service worker as a trusted context to deploy security applications.
To this end, we propose and develop a framework, SWAPP (Service Worker APplication Platform), for implementing security appliances by leveraging the unique capabilities of a service worker. Not only can SWAPP protect the aforementioned attack surfaces but also be used to implement defense mechanisms for traditional web attacks such as Cross-Site Scripting (XSS), data leakage, or side-channel attacks. We develop several defenses for traditional attacks using SWAPP and show that they are easier to develop, have lesser installation requirements, and are effective compared to existing solutions.
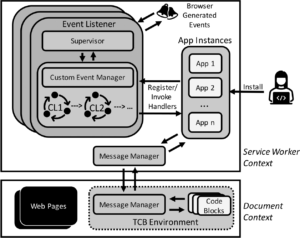
SOURCE CODE
SW-Scanner’s source code is released in github. Please check it.
SWAPP’s source code is released in github. Please check it.
PUBLICATIONS
SWAPP: A New Programmable Playground for Web Application Security.
Phakpoom Chinprutthiwong, Jianwei Huang, Guofei Gu.
In Proc. of the 31st USENIX Security Symposium (Security’22) Boston, USA, August 2022. [pdf] [bib]
The Service Worker Hiding in Your Browser: The Next Web Attack Target?
Phakpoom Chinprutthiwong, Raj Vardhan, GuangLiang Yang, Yangyong Zhang, Guofei Gu.
In of the 24th International Symposium on Research in Attacks, Intrusions and Defenses (RAID’21) Spain, October 2021. [pdf] [bib]
Security Study of Service Worker Cross-Site Scripting.
Phakpoom Chinprutthiwong, Raj Vardhan, GuangLiang Yang, Guofei Gu.
In Proc. of 2020 Annual Computer Security Applications Conference (ACSAC’20) USA, December 2020. [pdf] [bib]