INTRODUCTION
The research objective of the proposal is to address the challenges in the secure composition of microservices in the pervasive, distributed user-to-edge-to-cloud continuum of NextG network systems. The timeliness of NextG and the application on essential, life-critical services such as autonomous vehicles or telesurgery easily complicate the security and reliability requirements with dynamically varying demands. New challenges emerge such as the gap toward secure-by-design microservices, lack of programmable, zero-trust security primitives, and the complexity of verifying the multi-faceted security properties across a massive amount of microservices.
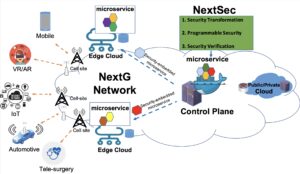
This project proposes a revolutionary construct of secure architecture for NextG, and a resulting frame- work called NextSec. The project consists of three research thrusts: Thrust I introduces the role of Security Transformers, a static and deploy-phase entity which transforms microservices into ones embedded with the defined security properties, including system, programming language, network, data-plane and control-plane properties. Thrust II adds the programming interfaces to the transformed microservices, to allow flexible and dynamic specification of security responses and security apps, with fine-grained visibility of system contexts and zero trust support. Thrust III extends the verification method of Maximal Causality Reduction (MCR) to verify the logical ordering of security properties, path-sensitive information flows across microservices, and the appropriate composition of security properties. The framework will be evaluated on Texas A&M Commercial 4G/5G Advanced Wireless Application Research Environment (AWARE) testbed, to show the compatibility, security, and performance benefit of the NextSec construct, with verification supported by the proposed MCR framework.
PIs
- PI: Guofei Gu (Texas A&M University)
- Co-PIs: Jeff Huang, Chia-Che Tsai, Walt Magnussen (Texas A&M University)
Publications
- Farabi Mahmud, Sungkeun Kim, Harpreet Singh Chawla, EJ Kim, Chia-Che Tsai, Abdullah Muzahid, “Attack of the Knights:Non Uniform Cache Side Channel Attack.” in Proceedings of the 39th Annual Computer Security Applications Conference (ACSAC’23), December 2023.
- Lei Xu, Yangyong Zhang, Phakpoom Chinprutthiwong, and Guofei Gu. “Automatic Synthesis of Network Security Services: A First Step.” In Proc. of the 32nd International Conference on Computer Communication and Networks (ICCCN’23), Hawaii, USA, July 2023. (Invited paper) [pdf] [bib]
- Huancheng Zhou, Sungmin Hong, Yangyang Liu, Xiapu Luo, Weichao Li, Guofei Gu. “Mew: Enabling Large-Scale and Dynamic Link-Flooding Defenses on Programmable Switches.” In Proc. of the 44th IEEE Symposium on Security and Privacy (S&P’23), May 2023. [pdf] [bib] (Release info)
- Sungmin Hong, Lei Xu, Jianwei Huang, Hongda Li, Hongxin Hu, Guofei Gu. “SysFlow: Towards a Programmable Zero Trust Framework for System Security.” In IEEE Transactions on Information Forensics and Security (TIFS), 2023. [pdf] [bib] (Release info)
Source Code
- SysFlow: an innovative programmable system security framework to enable unified, dynamic, and fine-grained Zero Trust security control for system resources. Source code is released at https://github.com/successlab/sysflow.
- Mew: A new P4-based memory-efficient and runtime adaptable link-flooding defense system! The source code is available here.
- NesTEE: an intra-process isolation mechanism for microservices on confidential computing platforms.
Sponsors
![]()