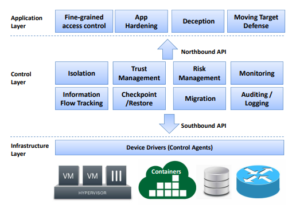
This project thus proposes S2OS, an SDI-defined Security OS, which offers an easy-to-use, programmable security model for monitoring and dynamically securing applications. S2OS aims to abstract security capabilities and primitives at various layers, thus providing unified programmability and controllability so that any security policy or procedure can be easily and dynamically programmed at infrastructure scale. We anticipate S2OS could unlock a wide range of unprecedented security opportunities, including fine-grained and dynamic security programmability at infrastructure scale, and information flow tracking across an entire infrastructure.
Read our position paper for more technical details. Read more about the goals and funding for this project.
S2OS is a $3M multi-institute project funded by NSF and VMWare.
Faculty PIs
 |
Guofei Gu, Lead PI Professor, Texas A&M University |
 |
Associate Professor, Clemson University |
 |
Associate Professor, University of Colorado at Boulder |
 |
Associate Professor, Ohio State University |
 |
Associate Professor, The University of North Carolina at Chapel Hill |
Publications
- Chia-Che Tsai, Jeongsok Son, Bhushan Jain, John McAvey, Raluca Ada Popa, and Donald E. Porter. “Civet: An Efficient Java Partitioning Framework for Hardware Enclaves”, in Proceedings of the 29th USENIX Security Symposium (USENIX Security ’20), Boston, MA, August 2020. [pdf]
- Hangchen Yu, Arthur Peters, Amogh Akshintala, Christopher J. Rossbach, “Automatic Virtualization of Accelerators”, In Proceedings of the Twenty-Fifth International Conference on Architectural Support for Programming Languages and Operating Systems (ASPLOS ’20), March 16–20, 2020, Lausanne, Switzerland. [pdf]
- Jaehyun Han, Zhiqiang Lin, and Donald E. Porter, “On the Effectiveness of Behavior-based Ransomware Detection”, Conditionally Accepted into the Proceedings of the 16th EAI International Conference on Security and Privacy in Communication Networks (SecureComm 2020).
- Zili Meng, Minhu Wang, Jiasong Bai, Mingwei Xu, Hongzi Mao and Hongxin Hu. “Interpreting Deep Learning-Based Networking Systems”, In Proceedings of the ACM SIGCOMM Conference (SIGCOMM 2020), New York City, USA, August 10-14, 2020. [pdf] (Release info)
- Jiasong Bai, Menghao Zhang, Guanyu Li, Chang Liu, Mingwei Xu and Hongxin Hu. “FastFE: Accelerating ML-based Traffic Analysis with Programmable Switches”, In Proceedings of the 1st Workshop on Secure Programmable Network Infrastructure (SPIN 2020), co-located with SIGCOMM 2020, New York, USA, August 10, 2020. [pdf]
- Juan Wang, Shirong Hao, Hongxin Hu, Hongda Li, Wenhui Zhang, Jun Xu and Peng Liu. “S-Blocks: Lightweight and Trusted Virtual Security Function with SGX”, IEEE Transactions on Cloud Computing (TCC), 2020. [pdf]
- Feng Xiao, Jinquan Zhang, Jianwei Huang, Guofei Gu, Dinghao Wu, Peng Liu. “Unexpected Data Dependency Creation and Chaining: A New Attack to SDN.” In Proc. of the 41st IEEE Symposium on Security and Privacy (S&P’20), San Francisco, CA, May 2020. [pdf] [bib] (Release info)
- Menghao Zhang, Guanyu Li, Shicheng Wang, Chang Liu, Ang Chen, Hongxin Hu, Guofei Gu, Qi Li, Mingwei Xu, and Jianping Wu. “Poseidon: Mitigating Volumetric DDoS Attacks with Programmable Switches.” In Proc. of the Network and Distributed System Security Symposium (NDSS’20), San Diego, California, Feb. 2020. [pdf] [bib]
- Jiahao Cao, Renjie Xie, Kun Sun, Qi Li, Guofei Gu, Mingwei Xu. “When Match Fields Do Not Need to Match: Buffered Packets Hijacking in SDN.” In Proc. of the Network and Distributed System Security Symposium (NDSS’20), San Diego, California, Feb. 2020. [pdf] [bib]
- Fei Ding, Hongda Li, Feng Luo, Hongxin Hu, Rong Cheng, Hai Xiao, and Rong Ge. “DeepPower: Non-intrusive and Deep Learning-based Detection of IoT Malware Using Power Side Channels”, In Proceedings of 15th ACM ASIA Conference on Computer and Communications Security (ASIACCS ’20), Taipei, Taiwan, June 2020. [pdf]
- Shuhe Wang, Zili Meng, Chen Sun, Minhu Wang, Mingwei Xu, Jun Bi, Tong Yang, Qun Huang and Hongxin Hu. “SmartChain: Enabling High-Performance Service Chain Partition between SmartNIC and CPU”, In Proceedings of 2020 IEEE International Conference on Communications (ICC ’20), Dublin, Ireland, June 2020. (Best Paper Award) [pdf]
- Guanyu Li, Menghao Zhang, Chang Liu, Xiao Kong, Ang Chen, Guofei Gu, Haixin Duan, Mingwei Xu. “NetHCF: Enabling Line-rate and Adaptive Spoofed IP Traffic Filtering.” In Proc. of the 27th IEEE International Conference on Network Protocols (ICNP’19), Chicago, Illinois, USA, October 7-10, 2019 (Acceptance rate 19.5%=41/210) [pdf] [bib]
- Guangliang Yang, Jeff Huang, Guofei Gu. “Iframes/Popups Are Dangerous in Mobile WebView: Studying and Mitigating Differential Context Vulnerabilities.” In Proc. of the 28th USENIX Security Symposium (Security’19), Santa Clara, CA, August 2019. [pdf] [bib]
- Jiahao Cao, Qi Li, Renjie Xie, Kun Sun, Guofei Gu, Mingwei Xu, and Yuan Yang. “The CrossPath Attack: Disrupting the SDN Control Channel via Shared Links”. In Proc. of the 28th USENIX Security Symposium (Security’19), Santa Clara, CA, August 2019. [pdf] [bib]
- Mohammad Hashemi, Greg Cusack, Eric Keller. “Towards Evaluation of NIDSs in Adversarial Setting,”3rd ACM CoNEXT Workshop on Big DAta, Machine Learning and Artificial Intelligence for Data Communication Networks (Big-DAMA), Dec, 2019. [pdf]
- Greg Cusack, Maziyar Nazari, Sepideh Goodarzy, Prerit Oberai, Eric Rozner, Eric Keller. (poster) “Efficient Microservices with Elastic Containers”. The 15th International Conference on emerging Networking EXperiments and Technologies (CoNEXT), Dec, 2019. [pdf]
- Menghao Zhang, Jiasong Bai, Guanyu Li, Zili Meng, Hongda Li, Hongxin Hu and Mingwei Xu. “When NFV Meets ANN: Rethinking Elastic Scaling for ANN-based NFs”, In Proceedings of IEEE ICNP 2019 HDR-Nets Workshop (HDR-Nets 2019), Chicago, IL, USA, October 7, 2019. [pdf]
- Chaoshun Zuo, Haohuang Wen, Zhiqiang Lin, and Yinqian Zhang. “Automatic Fingerprinting of Vulnerable BLE IoT Devices with Static UUIDs from Mobile Apps”. In Proceedings of the 26th ACM Conference on Computer and Communications Security (CCS’19), London, UK. November 2019 [pdf]
- Huibo Wang, Pei Wang, Yu Ding, Mingshen Sun, Yiming Jing, Ran Duan, Long Li, Yulong Zhang, Tao Wei, and Zhiqiang Lin. “Towards Memory Safe Enclave Programming with Rust-SGX”. In Proceedings of the 26th ACM Conference on Computer and Communications Security (CCS’19), London, UK. November 2019 [pdf]
- Wubing Wang, Yinqian Zhang, and Zhiqiang Lin. “Time and Order: Towards Automatically Identifying Side-Channel Vulnerabilities in Enclave Binaries”. In Proceedings of the 22nd International Symposium on Research in Attacks, Intrusions and Defenses (RAID’19), September 2019. [pdf]
- Hongxin Hu, Wonkyu Han, Sukwha Kyung, Gail-Joon Ahn, Ziming Zhao, Hongda Li, and Juan Wang. “Towards a Reliable Firewall for Software-Defined Networks. ” In Computers & Security (COSE), 2019. [pdf]
- Zili Meng, Jun Bi, Haiping Wang, Chen Sun and Hongxin Hu. “MicroNF: An Efficient Framework for Enabling Modularized Service Chains in NFV. ” In IEEE Journal of Selected Areas in Communications (JSAC), 2019. [pdf]
- Mengyuan Li, Yinqian Zhang, Zhiqiang Lin, Yan Solihin. Exploiting Unprotected I/O Operations in AMD’s Secure Encrypted Virtualization”, In Proceedings of the 2019 USENIX Security Symposium (USENIX Security’19), Santa Clara. August 2019 [pdf]
- Omar Alrawi, Chaoshun Zuo, Ruian Duan, Ranjita Kasturi, Zhiqiang Lin, Brendan Saltaformaggio. “The Betrayal At Cloud City: An Empirical Analysis Of Cloud-Based Mobile Backends”, In Proceedings of the 2019 USENIX Security Symposium (USENIX Security’19), Santa Clara. August 2019. [pdf]
- Huibo Wang, Erick Bauman, Vishal Karande, Zhiqiang Lin, Yueqiang Cheng, Yinqian Zhang. “Running Language Interpreters Inside SGX: A Lightweight Legacy-Compatible Script Code Hardening Approach”. In Proceedings of the 14th ACM Asia Conference on Computer and Communications Security (ASIACCS’19), July 2019. [pdf]
- Jiongyi Chen, Chaoshun Zuo, Wenrui Diao, Shuaike Dong, Qingchuan Zhao, Menghan Sun, Zhiqiang Lin, Yinqian Zhang, and Kehuan Zhang. “Your IoTs Are (Not) Mine: On the Remote Binding Between IoT Devices and Users”. In Proceedings of the 49th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN’19). June 2019 [pdf]
- Zhilong Zheng, Jun Bi, Heng Yu, Haiping Wang, Chen Sun, Hongxin Hu and Jianping Wu. “Octans: Optimal Placement of Service Function Chains in Many-Core Systems.” In Proc. of the 37th IEEE International Conference on Computer Communications (INFOCOM’19), Paris, France, April 29-May 2, 2019. [pdf]
- Qingchuan Zhao, Chaoshun Zuo, Giancarlo Pellegrino, and Zhiqiang Lin. “Geo-locating Drivers: A Study of Sensitive Data Leakage in Ride-Hailing Services”. In Proceedings of the 26th ISOC Network and Distributed System Security Symposium (NDSS’19), San Diego, CA, February 2019 [pdf]
- Yangyong Zhang, Lei Xu, Abner Mendoza, Guangliang Yang, Phakpoom Chinprutthiwong, Guofei Gu. “Life after Speech Recognition: Fuzzing Semantic Misinterpretation for Voice Assistant Applications.” In Proc. of the Network and Distributed System Security Symposium (NDSS’19), San Diego, California, Feb. 2019.
- Amogh Akshintala, Bhushan Jain, Chia-Che Tsai, Michael Ferdman, and Donald E. Porter. “x86-64 Instruction Usage among C/C++ Applications.” In Proceedings of the 12th ACM International Systems and Storage Conference (SYSTOR ’19), Haifa, Israel, June 2019. [pdf]
- Hongda Li, Feng Wei and Hongxin Hu. “Enabling Dynamic Network Access Control with Anomaly-based IDS and SDN.” In Proc. of ACM International Workshop on Security in Software Defined Networks and Network Function Virtualization (SDN-NFV Security’19), Richardson, TX, USA, March 27, 2019. [pdf]
- Oliver Michel, John Sonchack, Eric Keller, Jonathan M. Smith. PIQ: Persistent Interactive Queries for Network Analytics. ACM Workshop on Security in Software Defined Networks & Network Function Virtualization (SDN-NFV Sec’19), March, 2019. [pdf]
- Marcelo Abranches, Sepideh Goodarzy, Maziyar Nazari, Shivakant Mishra, Eric Keller. Shimmy: Shared Memory Channels for High Performance Inter-Container Communication. USENIX Workshop on Hot Topics in Edge Computing (HotEdge), July, 2019. [pdf]
- Aimee Coughlin, Greg Cusack, Jack Wampler, Eric Keller, Eric Wustrow. Breaking the Trust Dependence on Third Party Processes for Reconfigurable Secure Hardware. ACM/SIGDA International Symposium on Field-Programmable Gate Arrays (FPGA) (full paper), Feb, 2019. [pdf]
- Mohammad Hashemi, Greg Cusack, Eric Keller. Stochastic Substitute Training: A General Approach to Craft Adversarial Examples against Defenses which Obfuscate Gradients. ACM Workshop on Artificial Intelligence and Security (AISec), Oct., 2018. [pdf]
- Wenbo Ding and Hongxin Hu. “On the Safety of IoT Device Physical Interaction Control.” In Proc. of the 25th ACM Conference on Computer and Communications Security (CCS’18), Toronto, Canada, October 15-19, 2018. [pdf]
- Haopei Wang, Guangliang Yang, Phakpoom Chinprutthiwong, Lei Xu, Yangyong Zhang, Guofei Gu. “Towards Fine-grained Network Security Forensics and Diagnosis in the SDN Era.” In Proc. of the 25th ACM Conference on Computer and Communications Security (CCS’18), Toronto, Canada, October 2018. (Acceptance rate: 16.6%=134/809) [pdf] [bib]
- Hongda Li, Hongxin Hu, Guofei Gu, Gail-Joon Ahn, Fuqiang Zhang. “vNIDS: Towards Elastic Security with Safe and Efficient Virtualization of Network Intrusion Detection Systems.” In Proc. of the 25th ACM Conference on Computer and Communications Security (CCS’18), Toronto, Canada, October 2018. (Acceptance rate: 16.6%=134/809) [pdf] [bib]
- Menghao Zhang, Guanyu Li, Lei Xu, Jun Bi, Guofei Gu, Jiasong Bai. “Control Plane Reflection Attacks in SDNs: New Attacks and Countermeasures.” In Proc. of the 21st International Symposium on Research in Attacks, Intrusions and Defenses (RAID’18), Heraklion, Greece, September 2018. (Acceptance rate: 22.8%=33/145) [pdf] [bib]
- Jing Zheng, Qi Li, Guofei Gu, Jiahao Cao, David K.Y. Yau, and Jianping Wu. “Realtime DDoS Defense Using COTS SDN Switches via Adaptive Correlation Analysis. ” In IEEE Transactions on Information Forensics and Security (TIFS), 2018. [pdf] [bib]
- Chen Sun, Jun Bi, Zili Meng, Tong Yang, Xiao Zhang and Hongxin Hu. “Enabling NFV Elasticity Control with Optimized Flow Migration. ” In IEEE Journal of Selected Areas in Communications (JSAC), Vol.36, No.10, 2018. [pdf]
- Zhilong Zheng, Jun Bi, Haiping Wang, Chen Sun, Heng Yu, Hongxin Hu, Kai Gao and Jianping Wu. “Grus: Enabling Latency SLOs for GPU-Accelerated NFV Systems.” In Proc. of the 26th IEEE International Conference on Network Protocols (ICNP’18), Cambridge, UK, September 24-27, 2018. [pdf]
- Zhilong Zheng, Jun Bi, Chen Sun, Heng Yu, Hongxin Hu, Zili Meng, Shuhe Wang, Kai Gao and Jianping Wu. “A GPU-Accelerated Elastic Framework for NFV.” In Proc. of the 2nd Asia-Pacific Workshop on Networking, (APNet’18), Beijing, China, August 2-3, 2018. [pdf]
- Kang Chen, Jianwei Liu, James Martin, Kuang-Ching Wang and Hongxin Hu. “Improving Integrated LTE-WiFi Network Performance with SDN based Flow Scheduling.” In Proc. of the 27th IEEE International Conference on Computer Communications and Networks (ICCCN’18), Hangzhou, China, July 30-August 2, 2018. [pdf]
- Seungwon Shin, Zhaoyan Xu, Yeonkeun Kim and Guofei Gu. “CloudRand: Building Heterogeneous and Moving-target Network Interfaces. ” In Proc. of the 27th International Conference on Computer Communication and Networks (ICCCN’18), Hangzhou, China, August 2018. (Invited paper) [pdf] [bib]
- Oliver Michel, John Sonchack, Eric Keller, Jonathan M. Smith. “Packet-Level Analytics in Software without Compromises.” In USENIX Workshop on Hot Topics in Cloud Computing (HotCloud), July 2018.
- Richard Skowyra, Lei Xu, Guofei Gu, Thomas Hobson, Veer Dedhia, James Landry, Hamed Okhravi. “Effective Topology Tampering Attacks and Defenses in Software-Defined Networks. ” In Proc. of the 48th IEEE/IFIP International Conference on Dependable Systems and Networks (DSN’18), Luxembourg, June 2018. [pdf] [bib]
- Chen Sun, Jun Bi, Zili Meng, Xiao Zhang and Hongxin Hu. “OFM: Optimized Flow Migration for NFV Elasticity Control.” In Proc. of the 26th IEEE/ACM International Symposium on Quality of Service (IWQoS’18), Banff, Alberta, Canada, June 4-6, 2018. [pdf]
- Abner Mendoza, Guofei Gu. “Mobile Application Web API Reconnaissance: Web-to-Mobile Inconsistencies & Vulnerabilities. ” In Proc. of the 39th IEEE Symposium on Security and Privacy (S&P’18), San Francisco, CA, May 2018. [pdf] [bib]
- Guangliang Yang, Jeff Huang, Guofei Gu, Abner Mendoza. “Study and Mitigation of Origin Stripping Vulnerabilities in Hybrid-postMessage Enabled Mobile Applications.” In Proc. of the 39th IEEE Symposium on Security and Privacy (S&P’18), San Francisco, CA, May 2018. [pdf] [bib] (Project website with source code release)
- Zili Meng, Jun Bi, Haiping Wang, Chen Sun and Hongxin Hu. “CoCo: Compact and Optimized Consolidation of Modularized Service Function Chains in NFV.” In Proc. of the 53rd IEEE International Conference on Communications (ICC’18), Kansas City, Missouri, USA, May 20-24, 2018. [pdf]
- Amogh Akshintala, Vance Miller, Donald E. Porter, and Christopher J. Rossbach. “Talk to My Neighbors Transport: Decentralized Data Transfer and Scheduling Among Accelerators.” Proceedings of the 9th Workshop on Systems for Multi-core and Heterogeneous Architectures (SFMA ’18), Porto, Portugal, April 2018. [pdf]
- Greg Cusack, Oliver Michel, Eric Keller. “Machine Learning-Based Detection of Ransomware Using SDN.” in ACM International Workshop on Security in Software Defined Networks & Network Function Virtualization (SDN-NFV Security). March, 2018
- Hongda Li, Fuqiang Zhang, Lu Yu, Jon Oakley, Hongxin Hu and Richard Brooks. “Towards Efficient Traffic Monitoring for Science DMZ with Side-channel Based Traffic Winnowing.” In Proc. of the ACM International Workshop on Security in Software Defined Networks and Network Function Virtualization (SDN-NFV Security’18), Tempe, Arizona, USA, March 21, 2018. [pdf]
- Juan Wang, Chengyang Fan, Jie Wang, Shirong hao, Yi li and Hongxin Hu. “Challenges Towards Protecting VNF with SGX.” In Proc. of the ACM International Workshop on Security in Software Defined Networks and Network Function Virtualization (SDN-NFV Security’18), Tempe, Arizona, USA, March 21, 2018. [pdf]
- Younghee Park, Hongxin Hu, Xiaohong Yuan and Hongda Li. “Enhancing Security Education Through Designing SDN Security Labs in CloudLab.” In Proc. of the 49th ACM Technical Symposium on Computer Science Education (SIGCSE’18), Baltimore, Maryland, USA, February 21-24, 2018. [pdf]
- Jethro G. Beekman and Donald E. Porter. “Challenges For Scaling Applications Across Enclaves.” Proceedings of the 2nd Workshop on System Software for Trusted Execution (SysTEX ’17), Shanghai, China, October 2017. [pdf]
- Guofei Gu, Hongxin Hu, Eric Keller, Zhiqiang Lin, Donald Porter. “Building a Security OS with Software Defined Infrastructure.” In Proc. of the Eighth ACM SIGOPS Asia-Pacific Workshop on Systems (APSys’17), India, September 2017. [pdf] [bib]
- Lei Xu, Jeff Huang, Sungmin Hong, Jialong Zhang, Guofei Gu. “Attacking the Brain: Races in the SDN Control Plane.” In Proc. of the 26th USENIX Security Symposium (Security’17), Vancouver, BC, Canada, August 2017. [pdf] [bib]
- Chen Sun, Jun Bi, Zhilong Zheng, Heng Yu and Hongxin Hu. “NFP: Enabling Network Function Parallelism in NFV.” In Proc. of the ACM SIGCOMM Conference (SIGCOMM’17), Los Angeles, CA, USA, August 21-25, 2017. [pdf]
Resources
Project in the news:
- “Building a Secure OS From the Ground Up“, Government Computer News, July 2017 (also highlighted in ACM TechNews July 12, 2017)
- “Researchers Land $3 Million to Build Cyberattack Defenses“, The Newsstand (SC), June 2017 (also highlighted in ACM TechNews June 12, 2017)
- “Gu, collaborators receive grant for groundbreaking cybersecurity project“, Texas A&M University, June 2017
Relevant downloads:
- ForenGuard: A new forensics tool for fine-grained SDN network security forensics and diagnosis. A demo release is available now. Please check out the virtual machine image (5GB!) link1, link2, and a guide for demo here.
- FRESCO: A modular, composable SDN security app development framework
- Graphene Library OS: a library OS for running Linux multi-process applications, with Intel SGX support
- Metis: a general framework to interpret diverse DL-based networking systems at deployment